
Swingby Testnet Bug Bounty Program
Add to Watchlist
Added to Watchlist
Reward pool
Not set
USD
Expected profit
~ $25 - 5,000
USD
Max participants
∞
No limit
DropsEarn score
Neutral
Normal, Low Risks
Details
About
Swingby is a decentralized cross-chain protocol which moves assets like Bitcoin and Ethereum between chains using decentralized custodians.
In more simple terms, the protocol allows users to move their digital assets such as Bitcoin onto alternative chains such as Ethereum and BNB opening up a whole world of DeFi capabilities such as lending and DEX interaction.
Swingby exists as 3 core products:
- Skybridge: Fast inter-blockchain swaps. Users can move their tokens between blockchains effortlessly without relying on any central custodians. Based on the latest developments in this field of research, skybridge utilises threshold signature cryptography (TSS) and multi-party computing (MPC) to secure its network.
- Staking: Stake Swingby (BEP-2) tokens using the Staking portal. Pre-network launch, staking is implemented natively into the binance chain. After full network launch, staking will be a method of incentivising users to participate in the network through ‘Float Staking’ and ‘Bonding’.
- Sky Pools: Unique any-to-any token conversions. Sky Pools combines the swap functionality of the Skybridge with already existing market leading liquidity providers such as Uniswap, Balancer and Binance DEX. Source tokens are bridged to their corresponding peg token, exchanged into the target token with user-specified price constraints, and then finally bridged back to the target native chain if necessary.
Rewards
Rewards can be paid to your wallet address in either Swingby tokens or stablecoins and the 24hr average market price will be used to calculate the exchange rate.
Please note that the Swingby protocol is currently in its testnet phase and once released to mainnet the reward payout packages will be increased.
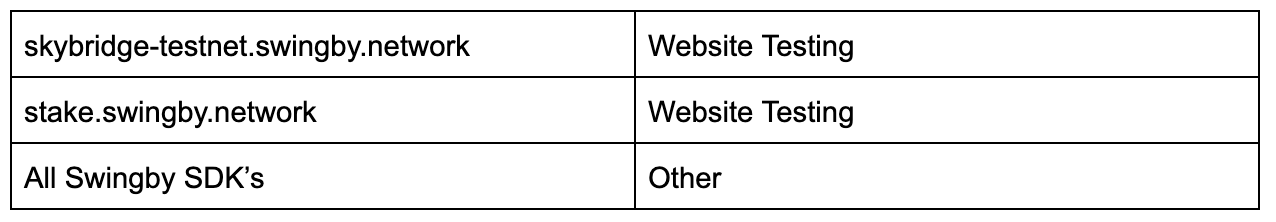
Targets

Out of scope (until mainnet launch)
Actions to avoid
- Testing using addresses/wallets other than your own
- Automated testing tools
- Destruction of data
Focus Area
- Vulnerabilities in distributed networks (Skybridge nodes).
- Vulnerabilities in swapping mechanics.
- Vulnerabilities in Swingby token staking payouts and tracking.
The following areas are out of scope
- Theoretical vulnerabilities without actual proof of concept.
- Email verification deficiencies, expiration of password reset links, and password complexity policies.
- Invalid or missing SPF (Sender Policy Framework) records (incomplete or missing SPF/DKIM/DMARC).
- Clickjacking/UI redressing with minimal security impact.
- Information disclosure with minimal security impact (E.g. stack traces, path disclosure, directory listings, logs).
- Internally known issues, duplicate issues, or issues which have already been made public.
- Tab-nabbing.
- Text injection.
- Self-XSS.
- Accessible Non-sensitive files and directories (e.g. README.TXT, LICENSE.TXT, robots.txt, gitignore, etc).
- Vulnerabilities only exploitable on out-of-date browsers or platforms.
- Vulnerabilities related to auto-fill web forms.
- Use of known vulnerable libraries without actual proof of concept.
- Lack of security flags in cookies.
- Issues related to unsafe SSL/TLS cipher suites or protocol version.
- Content spoofing.
- Cache-control related issues.
- Exposure of internal IP address or domains.
- Missing security headers that do not lead to direct exploitation.
- CSRF with negligible security impact (E.g. adding to favourites, adding to cart, subscribing to a non critical feature).
- Vulnerabilities that require root/jailbreak.
- Vulnerabilities that require physical access to a user’s device.
- Issues that have no security impact (E.g. Failure to load a web page).
- Assets that do not belong to Swingby.
- Social engineering / phishing attacks.
- Any DoS/DDoS activity using excess traffic that disrupts our services.
- Installation Path Permissions.
- Reports from automated tools or scans.
- Out-of-date software.
Vulnerability Classifications
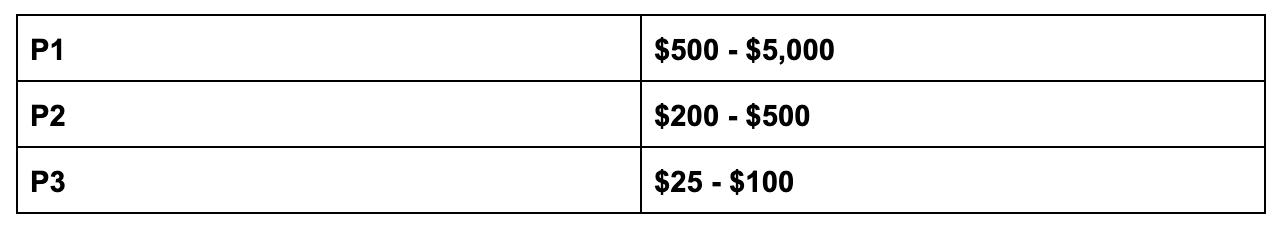
P1
- Vulnerabilities that expose private keys or any sensitive secrets.
- Vulnerabilities that result in a loss of funds (double spends, swap hijacking, network economics).
- Vulnerabilities in node consensus which could cause denial of service.
P2
- Vulnerabilities with similar impact as P1 vulnerabilities, but are dependent on specific prerequisites
- Other vulnerabilities that prevent swaps from being created or executed
P3
- Non-critical functionality
- Standard web exploits (XSS, CSRF, etc)
- Generic exploits
Policy
At Swingby, the security of our network and its users is our number one priority. For this reason, all reported bugs will be evaluated against the level of impact that it causes to both our network and/or it’s users.
About
Activity Type
Date
from 10 Sep 2020 12:00(UTC+3)
Registration
Closed
When Reward:
None
Event Status
Links

